Feb 16, 2021 The wordlists is a password attack tool that includes a wordlist and symlinks to several password files that are in the Kali Linux distro. What if we knew that target always used number passwords, now we can create a number password list instead of using all the characters, There are many un-secure content delivery networks available on the. Built-in Kali Linux wordlist rockyou.txt.
Hello Friends! Today in this tutorial I will show you that how to create wordlist file which you use over Brute Force Attack. In theprevious Brute Force Attack Blog, I show you the default word list. In which already password is saved and there is no guarantee that the password is present on the wordlist or not. So, here hackers use Information Gathering to find much information about the person and after finding all the information about Target then they will create wordlist file which is totally based on the information of the target.
DON’T MISS:- How to Hack Wi-Fi Using Fluxion Tool Advance Guide on Wi-Fi Hacking
There are so many methods to collect the information about the person by social media platforms, google etc. So, there are much more chances that the password is found on that wordlist which is created on the basis of information gathering. So, here we are going to create a custom password list which is totally based on the target information.
Let’s Begin 🙂
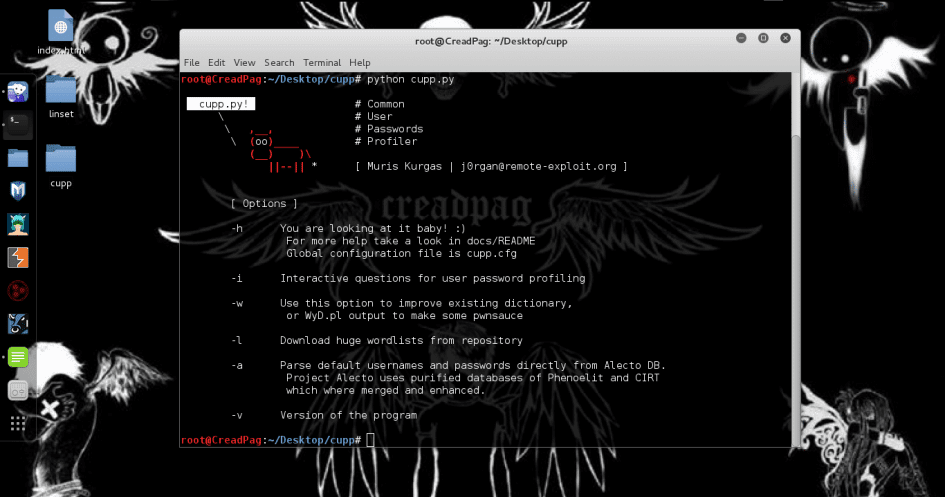
Firstly, we download a tool called cupp in your Kali Linux by clicking here. This is the tool which helps us to create a custom target based password list. After downloading this file open this file in your terminal and then type ./cupp.py .
This will show you the different options which you can use to make a password list. So, here we use the second option which is ‘-i’ in which this tool asks some questions about the target and then it will generate a wordlist. Just type ./cupp.py -i
Here, it asks some questions about the target like name, surname, nickname, and D.O.B. I fill all these details here then it will ask for his/her partner then fill these details also.
Then this will ask for the child’s name then fill these details too.
Now, it asks me for the pet name and company name.
Here, it ask us that you want to add some words which you want to add. If yes, then type ‘y’ and hit enter and then type the words which you want to add in the wordlist.
So, now it asks that you want special chars at the end of words? I type here yes. Because I want some special characters at the end of the word. Then it will ask that to add some random no.? I also type here ‘y’ to add random no. Now it asks for the Leet mode The leet mode is to add some special characters between your passwords like[email protected]
Now, your wordlist is generated on the basis of the information which you give. You can use this wordlist for any Brute Force Attack.
If you have any doubts and queries then do comment it below. I will definitely do answer it. 🙂
ALSO READ:- How To Hack Wifi Password Using Kali Linux
a
Before starting the attack lets have a small introduction about WPA/WPA2 .
What is WPA/WPA2
Wi-Fi Protected Access (WPA) and Wi-Fi Protected Access II (WPA2) are two security protocols and security certification programs developed by the Wi-Fi Alliance to secure wireless computer networks. The Alliance defined these in response to serious weaknesses researchers had found in the previous system, WEP (Wired Equivalent Privacy).
WPA became available in 2003. The Wi-Fi Alliance intended it as an intermediate measure in anticipation of the availability of the more secure and complex WPA2. WPA2 became available in 2004 and is a common shorthand for the full IEEE 802.11i (or IEEE 802.11i-2004) standard.
A flaw in a feature added to Wi-Fi, called Wi-Fi Protected Setup, allows WPA and WPA2 security to be bypassed and effectively broken in many situations. WPA and WPA2 security implemented without using the Wi-Fi Protected Setup feature are unaffected by the security vulnerability.
WPA2 has replaced WPA. WPA2, which requires testing and certification by the Wi-Fi Alliance, implements the mandatory elements of IEEE 802.11i. In particular, it includes mandatory support for CCMP, an AES-based encryption mode with strong security. Certification began in September, 2004; from March 13, 2006, WPA2 certification is mandatory for all new devices to bear the Wi-Fi trademark.
Requirements to start attack
- Kali Linux (Installed in virtual machine (or) as host).
- External WIFI card.
- A word-list containing passwords. (In kali you are having wordlist rockyou.txt which is located in /usr/share/wordlists)
Step 1
First we have to check our wifi card is connected with our device or not. To see that we have a command
ifconfig
Now you can see we are having wireless interface as wlan0 connected to our machine.
Step 2
To capture the packets of the wireless network we need to turn on our wifi card to monitering mode. To do that we have command
- airmon-ng start [interface name]
airmon-ng start wlan0
Kill all the process/PID which can create problems while cracking.
- kill [PID no.]
Step 3
Now we are in monitoring mode having interface wlan0mon. After entering into monitoring mode please check the interface name again to go further.

we can sniff the packets of the entire network and we can see how many accesspoints are around you. To do that
- airodump-ng [present interface name]
airodump-ng wlan0mon
Step 4
Now you are having list of Wifi accesspoints around you , select the desired once you want to crack. To do that
- airodump-ng -c [channel] –bssid [Target Mac] -w [file_name you want to save] [interface]

airodump-ng -c 1 –bssid FC:4A:E9:4B:01:8A -w 000 wlan0mon
Do not close this window because you will get handshake here.
Step 5
To crack the wifi password we need to have handshake i.e to connect any wifi router we need to exchange our key with the router to verify the Guinean user and if our key is correct we will get connected. Every time the user try to connect the exchange of keys take place and the process is called handshake.
Now we are going to take the advantage of this process . Only handshake happens when a user tries to connect to the route, as we can’t wait for the new user to connect .
we can disconnect the user already connected and those users who are disconnected tries to connect back to the route. In the mean time we can sniff handshake. To do this
- aireplay-ng -0 [no.of packets] -a [accesspoint mac] [interface]
airreply-ng -0 1000 -a FC:4A:E9:4B:01:8A wlan0mon
It will send Deauth packets to the users and disconnect them don’t stop this process until you get the handshake.
Kali Linux Password Wordlist Pdf
See we got the handshake. This handshake that we captured is saved in a file 000 that we have given in Step 4.
Step 6
The last and final step to get password . We are having a tool named Aircrack which will brute force the list of word-list password and tries to crack the wifi pin.
Rockyou Wordlist Kali Linux
To crack the password using Aircrack
- aircrack-ng [file containing handshake packets] -w [word-list containing passwords]
aircrack-ng 000.cap -w rockyou.txt
Sucessfully Cracked the wifi password.
Note: This method only works when you are having correct password in your word-list. If you are not having correct password in your word-list file then this attack is of no use.